
OWASP Top 10 2017: what’s new?
In autumn 2017, the OWASP project has published the updated Top 10 list of web apps vulnerabilities. The Top 10 is produced with the goal of empowering webdevs, security testing teams, and web product owners to ensure the apps they build are secure against the most critical flaws. This time, the data for the Top was submitted by 23 contributors covering 114,000 applications of all kinds, which makes the Top 10 impartial source of AppSec information.
As security testing is one of a1qa most in-demand services, we couldn’t pass the Top 10 release by. After analyzing the changes and novelties, we offer you to go through the main changes and learn what they mean in terms of the state of information security.
If you develop apps, ensure their quality, run penetration tests, or own the web app to run business – keep reading.
How has the OWASP Top 10 changed?
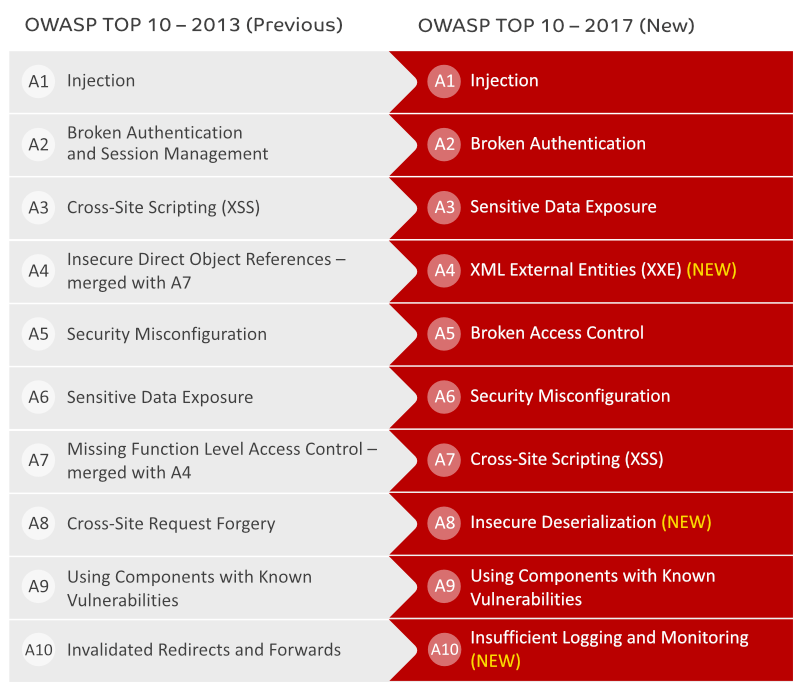
In general, OWASP Top 10 has welcomed three novelties and retired two that pose no such a severe threat. Aleksey Abramovich, Head of a1qa Security Testing Department, has commented on the recent changes.
New entries on the Top
XML External Entity, Insecure Deserialization, and Insufficient Logging and Monitoring – are the newcomers to the list.
“Together with the growing complexity of web solutions, there is constant growth in the variety of data and servers that generate it. Nevertheless, it’s not a rare case when new solutions are based on legacy principles that not always go in hand with the best practices. A good and illustrative example is simple server commands to extract critical data. An insecure XML processor may process the command without suspecting an authorized access:
<?xml version=”1.0″ encoding=”ISO-8859-1″?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM “file:///etc/passwd” >]>
<foo>&xxe;</foo>
In such an easy way, the intruder may gain access to the users list. The next possible step is the attempt to dig up passwords and get information from databases to gain control over the app,” comments Aleksey.
Another obvious change that took place since 2013 is the Insecure Direct Object References category merged with Missing Function Level Access Control into Broken Access Control category that occupied the fifth spot in the release version.
“I guess the two itmes have been merged as exploiting any of them the attacker has one goal in mind – gain unauthorized access to the system, private accounts and manipulate the system as desired. That’s why they were merged into one category”, Aleksey assumes.
What vulnerabilities have left the top?
Two of the vulnerbilities – CSRF and Unvalidated Redirects and Forwards – found no place on the list. Based on the OWASP data, they have dropped to the 13th and 25th spots respectively. What does it mean?
“Correct redirects and cross-site scripting plays a very important role when using advertisement, or there are complex, multi domain web sites. Today, online ads are crucial for millions of web businesses. That’s why testing redirects security is vital. The owner of the resource should be sure that the users data will be secured and they won’t get redirected to a maliciously crafted link or third-party web page. Today, the developers take serious measures to make users stay within their domain or redirected correctly.”
Injections are still No.1
Despite the changes mentioned above (three new vulnerabilities and two retirements), some vulnerabilities have stayed on Top 10 since 2010 and for the second year in a row Injection is the Top leader. How comes it that with the development of security practices there are still gaps that can be used by the abusers? Aleksey Abramovich answers the question.
“Since 2013, the security awareness has really got on the rise. Numerous secure coding best practices, data cleansing tools, and web tokens to secure their apps have been introduced. Unfortunately, all this didn’t make the app safer for users and most common security flaws remain the same.
Injection is still ranked No.1 and it’s easy to explain. There are many types of injections, SQL are probably the most common, but all of them are highly destructive, easy to perform, and therefore are responsible for a large number of public disclosures and security breaches.
Any injection attack occurs when unvalidated input comes from outside of the system and is embedded into the input stream. The variety of entry points is huge. Again, this type of attack is rather easy to exploit, it can be done from any kind of query. More often injections are found in legacy code, but at times developers generate them when coding, and the consequences can be very dramatic for the app owner.”
Penetration testing as a way to identify vulnerabilities
Certainly, the weaknesses on the list are only the most common ones. Secutiy checks should stretch far beyond them. However, checking the app against them is a good way to find the most common flaws that have to be fixed and improve the security of the app.
Will your website pass the OWASP Top 10 test? Order vulnerability scan by a1qa security experts.








